Security
researcher Patrick Wardle presented several security flaws in the video
conferencing software Zoom at the hacker conference Def Con. There is
still no patch for a zero day under MacOS. It can extend rights and thus
execute malware as an administrator. Zoom has already fixed several other
bugs.Online magazine The Verge had reported.
The vulnerability was
first discovered by Patrick Wardle ,
founder of the Objective-See Foundation , a non-profit
Mac OS security organization. Wardle detailed in a presentation at Def
Con last week how
Zoom's installer asks for a user password when installing or uninstalling, but
the automatic update feature, which is enabled by default, does not require a
password. Wardle discovered that Zoom's updater was owned and run by root.
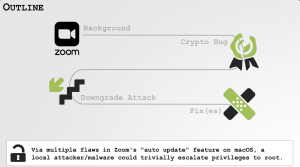
Enlarge / Highlights
on how Zoom's auto-update utility allows privilege escalation exploits, from
Patrick Wardle's Def Con talk.
This appears to be safe as
only Zoom clients can connect to the privileged daemon and can only extract
packages signed by Zoom. Zoom Video ... Certification Authority Apple
Root CA.pkgThe
problem is that this check can be bypassed by simply passing the
validation checker on the name of the package it is looking for ("
"). This means malicious actors can force Zoom to downgrade to a
buggy, less secure version, or even pass an entirely different package that
could allow them to gain root access to the system.
According
to the report, the security problem lies in Zoom's update function, which, for
example, installs updates or removes the software. Although this checks whether
a downloaded package has been cryptographically signed, an error in the
checking method means that the updater can be given any certificate with the
same name as Zoom's signing certificate.
This
would allow attackers to bypass the verification of the software to be
installed and execute malware, for example. The malware is executed by the Zoom
updater with administrator rights. However, the vulnerability can only be
exploited if attackers already have access to the affected person's system, but
then they can extend their rights and have far-reaching access to the affected
system.
Wardle
reported the vulnerability back in December 2021, and a first fix introduced
another bug that allowed the vulnerability to continue to be exploited, but in
a more complicated way, Wardle explained to The Verge. After eight months, he
said, he has now decided to make the vulnerability public, even though it
remains unfixed.
"For
me, it was kind of problematic because I wasn't just reporting the bugs to
Zoom, I was reporting the bugs and how to fix the code," Wardle said.
"So it was really frustrating to wait six, seven, eight months and know
that all the Mac versions of Zoom were sitting on users' computers and were vulnerable."
With the release, Wardle hopes that the bug, which he said was very easy to
fix, will now finally be fixed.
Shortly
before the conference, Zoom had released an update to fix the flaw. According
to The Verge, the update file is now moved to a folder that belongs to the user
root. Since the user's read and write permissions are also copied when the file
is copied, the user can continue to modify the file - and attackers can
continue to exchange the file and expand their permissions.
Matt
Nagel, Zoom's PR officer for security and privacy, said in a statement to The
Verge: "We are aware of the newly reported vulnerability in Zoom
Auto-Updater for macOS and are working diligently to fix it."